That is it, you have just unpacked UPX!!! Based on type and complexity of Packer, unpacking operation may vary in terms of time and difficulty. Usually this is the first instruction or it will be present after first few instructions based on the UPX version. Ultimate Packer for Executables. Finally after fixing import table, run the new unpacked EXE to make sure it is perfect! The UPX Unpacker plug-in works on packed malware executables and can handle a file even if it has been packed with UPX and modified manually so that UPX cannot be used directly to unpack the file, because internal structures have been modified, for example the names of the sections have been changed from UPX to XYZ, or the version number of the UPX format has been changed from 1. 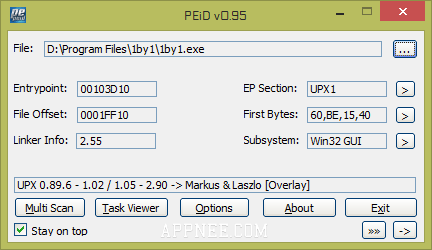
| Uploader: | Sashura |
| Date Added: | 15 January 2015 |
| File Size: | 43.81 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 61380 |
| Price: | Free* [*Free Regsitration Required] |
Popular Ring 3 Debugger. In addition to pointed locations you can do your own comparison on Strings, Resources, code fragments etc… and see the remarkable similarity.
Usually this is the first instruction or it will be present after first few instructions based on the UPX version. Now start step by step tracing with F7 and soon you will encounter a JMP instruction which will take us to actual OEP in the original program. The resulted file will also be saved unpacked. When you pack any Executable with UPX, all existing sections text, data, rsrc etc are compressed.
All versions of UPX are supported, from the obsolete ynpacker versions generid to 0.

Almost the same strings, Strings containing xAurora has there counterparts with Maxthon, Same Class names etc etc…. This video demonstration uses slightly different way to put a hardware breakpoint than described in the article. May be this cannot be changed since this Data Object name is referenced from many other places in the code. Now you can open files compressed with UPX even without knowing that!
However for most of the packers, we need to use advanced tool called ImpRec Import Reconstructor. Now you can open these obfuscated files even without knowing that: And scolle down to location 0xED0.
Although you can use any debugger, OllyDbg is one of the best ring 3 debugger for Reverse Engineering with its useful plugins.
Now launch the ImpREC tool and select the process that you are currently debugging. Uncovering hidden process on Windows system. The UPX Unpacker plug-in works on packed malware executables and can handle a file even if it has been packed with UPX and modified manually so that UPX cannot be used directly to unpack the file, because internal structures have been modified, for example the names of the sections have been changed from UPX to XYZ, or the version number of the UPX format has been changed from 1.
NO then remove it by by right clicking on it and then from the popup menu, click on 'Delete Thunks'. So we need to unpack pid EXE before looking at code. That is it, you have just unpacked UPX!!! Previously, losing the PE file header rendered the executable completely inoperable and unrepairable.
Here are the steps shown in video. UPX is the basic Packer and serves as great example for anyone who wants to gendric Unpacking. I have not included steps to verify the accuracy of OEP and rebuilding of import sections here because I want to keep this as simple as possible. Now run the final fixed executable to see if everything is alright.
Faster way to enumerate process heaps.
xAuroraRC1-Final-Lite
Now click on 'Get Genric to retrieve all the imported functions. You will see all the import functions listed under their respective DLL names.
When this is open, you can set priority for a selected plug-in. You will see xAurora starts in the background.
2. Unpacking
This unpacked EXE will not run because we have not fixed the import generiic and the OEP may not be accurate but this generated file just serves our purpose. Before we begin with unpacking exercise, lets try to understand the working of UPX.
If is stops at any splash screen press ok to continue till the browser interface shows up. It provides multiple methods to trace the API functions as well as allow writing custom plugins.
Ultimate Packer for Executables. Ok now we can see that xAurora is packed with PECompact.

Comments
Post a Comment